TTO - WannaCry (WannaCrypt or Wcry) is causing a massive earthquake in the last few days (75,000 cases in 99 countries).
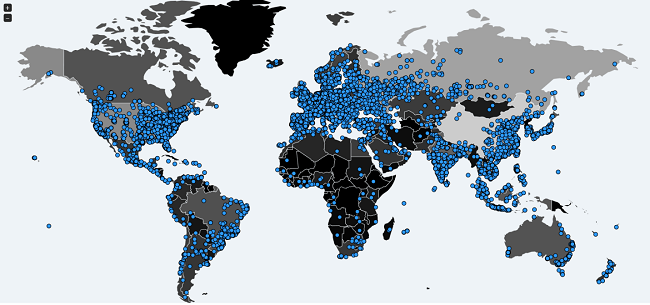
Map showing countries with computers infected with WanaCry, up to 03:00pm on May 15
(https://intel.malwaretech.com/botnet/wcrypt)
This article is intended to provide an insight into the Malware, clarifying the risks faced by future computer users, and explaining how difficult to recover data.
The amount that the bad guys required to recover data is $ 300 per case.
Wanna.Cry's victim is a Windows computer with the EternalBlue MS17-010 security hole (which includes all Windows operating systems to Windows
What is ransomware?
To understand what ransomware is, we first learn a little about Malware in general. Accordingly, there are two important stages in the life cycle of Malware: spreading and executing malicious behavior.
Spreading is the way malicious code enters a victim's computer, such as spreading email messages with attached file that contain malicious files, downloading malicious files; Wanna.Cry uses both exploits of Windows security holes and send malicious email attachments.
Executing malicious behavior is very diversed, such as file deletion, denial of service attacks, identity theft and victim extortion.
As defined by TrendMicro, ransomware is a type of malware that restricts computer users from accessing their systems. It can lock the computer screen, or lock the files on the user's computer until the ransom is received.
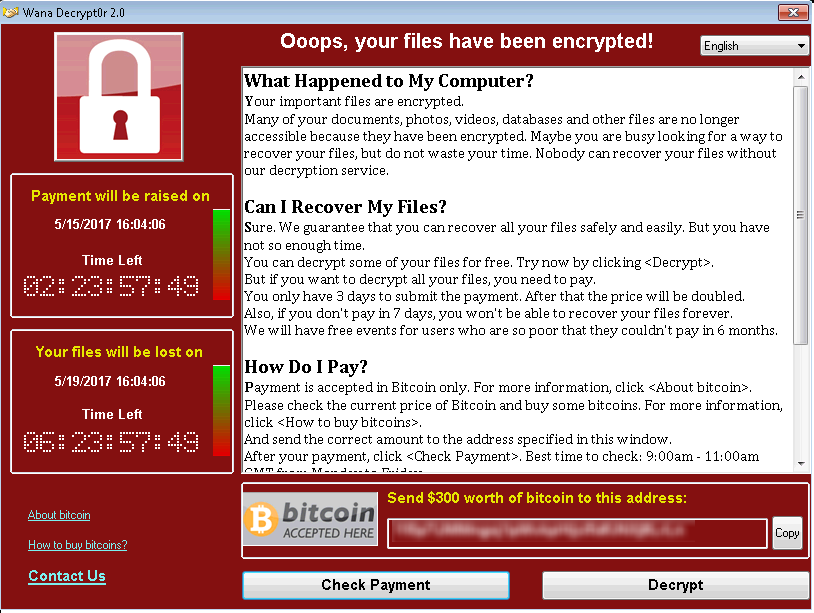
Information screen on Wanna.Cry ransomware
Wanna.Cry is a new malware?
According to Symantec statistics, the amount of malware is discovered as well as the amount of extorted money hacker’s requests increased constantly. Since malware information has only been spreaded on the mass media in recent times, it is easy to mistakenly believe that this is a new type of malware.
However, as mentioned above, extortion malware is different from the other malware is the way of malicious method. This largely depends on the attacker's intent and less technical barriers.
Indeed, the first malware AIDS Trojan appeared very early in 1989. To decrypt data the victim must send $ 189 to a mailbox in Panama. Even in 1996, two researchers at Columbia University published technical details that could be used to encrypt and blackmail users.
The main idea is that malicious code generates a symmetric key at random, and then uses this key to encrypt the user's data.
Next, the malware attempts to encrypt the key with the asymmetric key with the information contained in the malware. Wanna.Cry use RSA-2048.
With the characteristics of the asymmetric encryption algorithm, only the corresponding secret key holder (here is the bad guy) can decrypt.
With current calculating power, attacking algorithms such as RSA using a large key length (eg 2048 bits) is completely impossible (taking many years).
To be deciphered, the victim must pay the ransom demanded by the bad guys. The danger here is that the bad guys can choose to pay by anonymous means (the payer does not know who he pays for and who is not).
Wanna.Cry choose the form of payment by bitcoin. By not being able to track who is receiving the money we would not be surprised if the amount of Malware goes bankrupt in the future. According to a Symantec report, in 2016 there were 357 million variants of Malware. What happens if all (or most) of these malicious code become extortion malicious code?
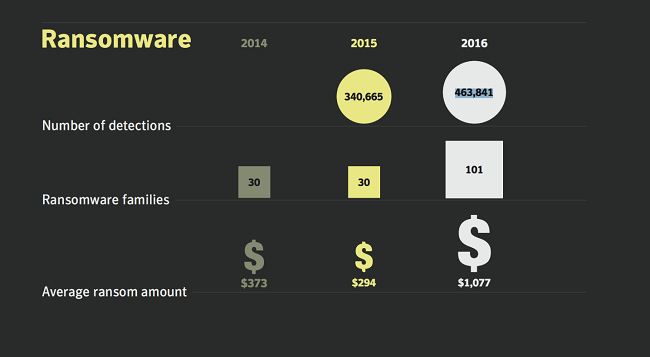
Statistics on Malware - Source: Symantec
Limit the damage of Wanna.Cry
As explained above, if the bad guys properly use the encryption algorithms, the effort to decrypt the data is almost impossible.
However, we can apply the following recommendations to minimize the possibility of this ransomware infection:
- Updated the latest patches of the operating system Windows is using from the Microsoft website.
- Check the operating system firewall to ensure that it is in "on" mode.
- Update the latest data for virus browser.
- Back up important data to external storage.
- Be cautious in opening attachments
- Look carefully before clicking on the paths of unknown origin, strange structure or shortened paths.
- Spreading to the community how to use computers responsibly.
Also, a simple way to prevent WanaCry infection is to ban portals related to SMBs such as ports 445, 139, and 3389. Alternatively, you can turn off the SMB protocol on your computer by running the following command in the command prompt ( Runs in Administrator mode.
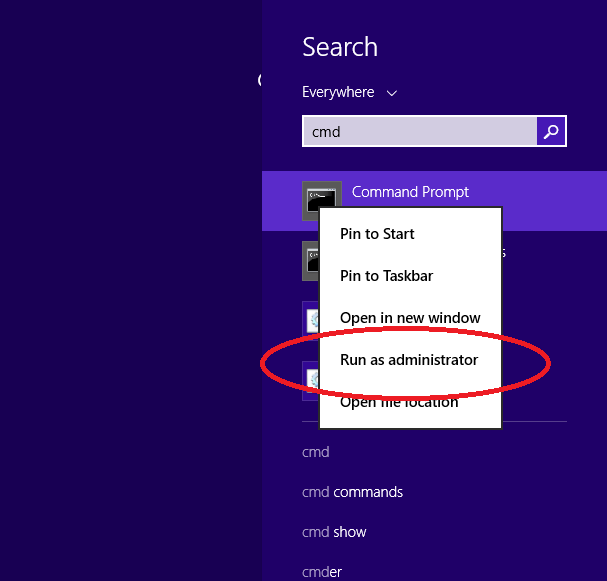
How to run the Command Prompt with Administrator privileges
Run the command: dism /online /norestart /disable-feature /featurename:SMB1Protocol
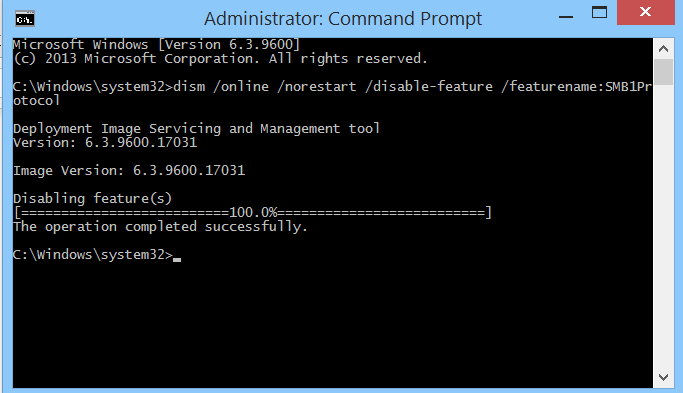
How to turn off SMB with dism
In addition, users should also check the existing shared folders on their computer. This helps limit the possibility of copying malicious files from other computers on the network to your computer.
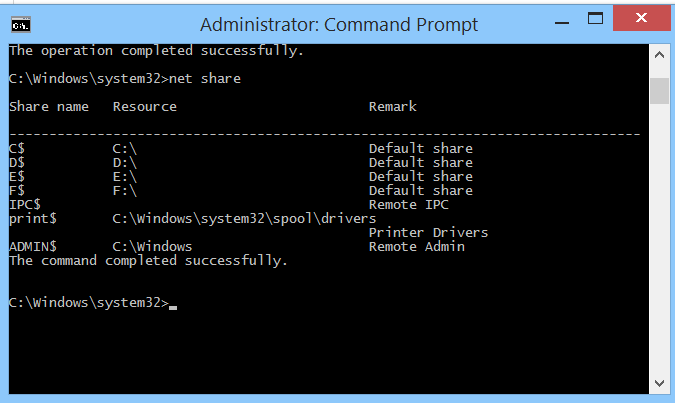
Check out the shared folders on your computer
Dr. PHẠM VĂN HẬU (Director of CNSC Information Security Center - University of Information Technology - VNU)
Source: tuoitre.vn







